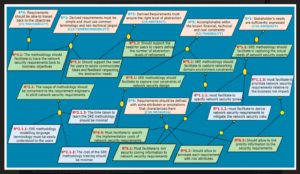
Top cybersecurity engineers are using planning tools like this one to re-think engineering for secure wireless networks hosting the internet of things. Image courtesy of the Journal of Cybersecurity and Privacy.
Most of us have taken an airplane trip in the last few years. You probably flew on a plane that had a touchscreen displayed on the back of the seat in front of you. You could pick from television shows and movies, as well as toggle to a screen that gave you the altitude, estimated arrival time and geo-location of the plane in real time.
This kind of customer experience is as common in airplanes as griping about seat-reclining etiquette, so most people take it for granted. You have one of these screens in your pocket all the time, so why not on a plane?
You’d be correct in assuming the basic tech for streaming video while flying 500 miles per hour is well-established. Impressive, objectively, but hardly groundbreaking in the 2020s.
The real challenge is to manage wireless data streams with different levels of accessibility security requirements without opening avenues for fanatics, hackers, thieves and hostile states to digitally invade the system.
Whether a black hat wants to crash the plane to further some political goal or whether they just want to steal your credit card number when you order a cocktail, you as a customer must access the same network that runs vital flight functions and monitoring, potentially opening security back doors.
What Is Network Security by Design?
Keeping such a complex wireless network system secure while still providing multiple layers of access and security levels (point-of-sale and content streaming vs. flight control and monitoring functions) requires planning from the very inception of designing the plane. This is called “security by design,” a process that puts network security requirements at the same level of priority as, say, developing the code running a motor moving the aileron up and down.
Security by design is not a new concept in digital systems, but the requirements have grown exponentially in complexity as devices and components develop increasing levels of autonomous function.
In 2020, the “internet of things,” reached a tipping point; today, there are more connected devices communicating over networks than people, according to IOT Analytics, a market research firm. Connected cars, smart home devices and industrial equipment now make up 11.7 billion of the 21.7 billion connected devices, worldwide – 54% as opposed to the 46% composed of phones, tablets and computers that connect human network users.
On airplanes, these autonomous components need to talk to each other and to human operators through multiple channels, and it’s vital to keeping the plane in the sky that each one of these channels is 100 percent secure.
That’s why the French aerospace industry has been involved in the IREHDO2 project – an obscure program (in the English-speaking world, at least) to develop secure-by-design avionics networks using giga-ethernet rather than expensive cabling. Partners like Airbus, the French national aerospace lab ONERA and the Directorate General of Civil Aviation (France’s version of the FAA) are involved in the multi-year research project.
Wired Networks Cost Companies Billions

Cabled networks in an aircraft can cost $50 million to install. A secure giga-ethernet avionics network could save millions and remove lots of weight in wires from the airframe, improving fuel efficiency.
Avionics software engineering researchers in a 2018 article in the journal Sensors pointed out why secure, wireless avionics networks are so important. Even when everything goes right, installing a cabled network in a plane can cost $50 million. Cabling installation problems and delays can cost a single manufacturer literally billions.
“Although this (wired) communication architecture meets the main avionics requirements, it leads at the same time to an inherent heterogeneity of the interconnection means and a large amount of cables and connectors, thus high integration costs,” the article states. “The costs related to cabling during the manufacturing and installation are actually between $14 million for an Airbus A320 to $50 million for an Airbus A787. Moreover, the cabling complexity is considered to be one of the main reasons behind the production delays of the Airbus A380, where the cost overruns have been estimated at $2 billion dollars.”
As a result of this effort to update established requirements engineering, software security requirements engineers start giving input to the team from the outset of planning. This was the key finding from the IREHDO2 project. In many network-building efforts to-date, engineers consider security measures separately in the process and graft them on as an extra function once other engineers have already established the basic design.
“Considering network security too late in the network development cycle would render additional costs and complexity,” IREHDO2 authors state in a 2021 paper in The Journal of Cybersecurity and Privacy. “The difference in the return of security investments considered at early or at late stages of the system development cycle can range from 12% to 21%. Therefore, it is necessary to examine network security at earlier stages, i.e., right from the planning stages of networks architecting. Indeed, bad network security requirements can lead to ineffective and costly security or worse, security holes in the network.”
Can Security by Design Be Applied to Any Computer Network System?
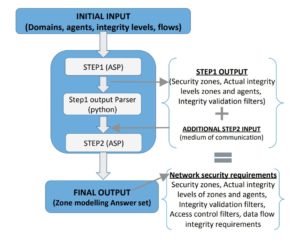
An example of refined modeling for secure networks. Image from a paper presented at the 2019 Symposium on Applied Computing in Cyprus
The upshot? The rise of the internet of things, 5G wireless internet, autonomous avionics devices and other trends pushing transactions and work online are forcing cybersecurity engineers to reengineer engineering.
Software engineers use decision-making and prioritization tools like KAOS (Keeping All Objectives Satisfied) and other logical rubrics as planning matrices for building networks. The client, developers, engineers and customers’ (all the stakeholders’) stated needs from a particular IT project funnel into the logical construct to map out the planned network’s operations.
The structure of the rubric guarantees disparate functions of the system can operate without running at cross purposes or compromising the function of any other system component.
Researchers for the IREHDO2 project took several of these different planning systems, integrated them, standardized the descriptive language and prescribed early entry of security engineers into the process.
This same cutting-edge secure network planning tool developed by the avionics experts in France’s IREHDO2 project can apply to any network with layered security levels. This latest engineering framework for considering cybersecurity can apply to any project, regardless of the kind of cryptography or network security zoning methods used to execute the secure requirements.
How Does SkillsetGroup IT Implement Security by Design for Clients?

Learn more about SkillsetGroup IT’s information technology consulting services, including specific expertise we provide, projects we service and other ways we can grow your business.
At SkillsetGroup IT, security is foundational.
Security by design is how we approach every consulting project, from designing aircraft control networks, to setting up electronic healthcare records systems with blockchain technology, to implementing ERP solutions for businesses of almost any size and more.
When we’re gauging your business needs, guiding your RFP process for software and equipment vendors, figuring out the level and type of IT staffing you need for a project, and bringing in talented IT professionals, securing your information is always at the forefront of our considerations.
For more information about how SkillsetGroup IT can bring transformational cybersecurity solutions and strategy to your business, contact us at (800) 774-1603.
REFERENCES
Romain Laborde et al
The Journal of Cybersecurity and Privacy
June 2021
“Top Security and Risk Trends for 2021”
Gartner Research
“State of the IoT 2020: 12 Billion IoT Connections, Surpassing non-IoT for the First Time”
Knud Lasse Lueth
IoT Analytics
Nov. 2020
“Annual Threat Assessment of the U.S. Intelligence Community”
Office of the Director of National Intelligence
April, 2021
“Introduction to KAOS Goal Modeling”
Erik Fredericks
Michigan State University College of Engineering
Ahmed Amari and Ahlem Mifdaoui
Sensors
November 2018
“Logic-based methodology to help security architects in eliciting high-level network security requirements”
Romain Laborde et al
2019 Symposium on Applied Computing in Cyprus
